Issues with traditional security:
- Traditional security is discontiguous configured site by site manually. Which is complex and is not easy to manage.
- Current security model is designed as per traditional architectures like on-prem Data centres services and Office users.
- Enterprises are moving towards multi-cloud environment with current on-prem security has many gaps to secure SAAS/IAAS/PAAS cloud solutions.
- Now customers with mobile security should not be only tagged to his machine,location or port.
- Business is changing sometimes requires fast service and security rules for required couple of hours only.
- This traditional security can provide some sort of security with in enterprise however when users are mobile and accessing cloud , REST API's interactions over internet.It requires new intelligent security design.
- There is a need of security model with full stack intelligence,proactiveness,analytics,IPS,IDS,malware protection,Sandbox and DNS layer security.
- Zero trust security model is required. Zero Trust is basically change in the traditional security best practices where inside users were considers as trusted users.
- But the problem is if any organisation has hosted everything on their backbone network like MPLS they will have all security appliances and policies in place.No one can access the inside network. However despite of having all security practices in place the network can still be compromised.What if, any of the inside user is compromised then entire security will be compromised.Most of these attacks happens from the inside.From outside it not so easy to crack the private network.
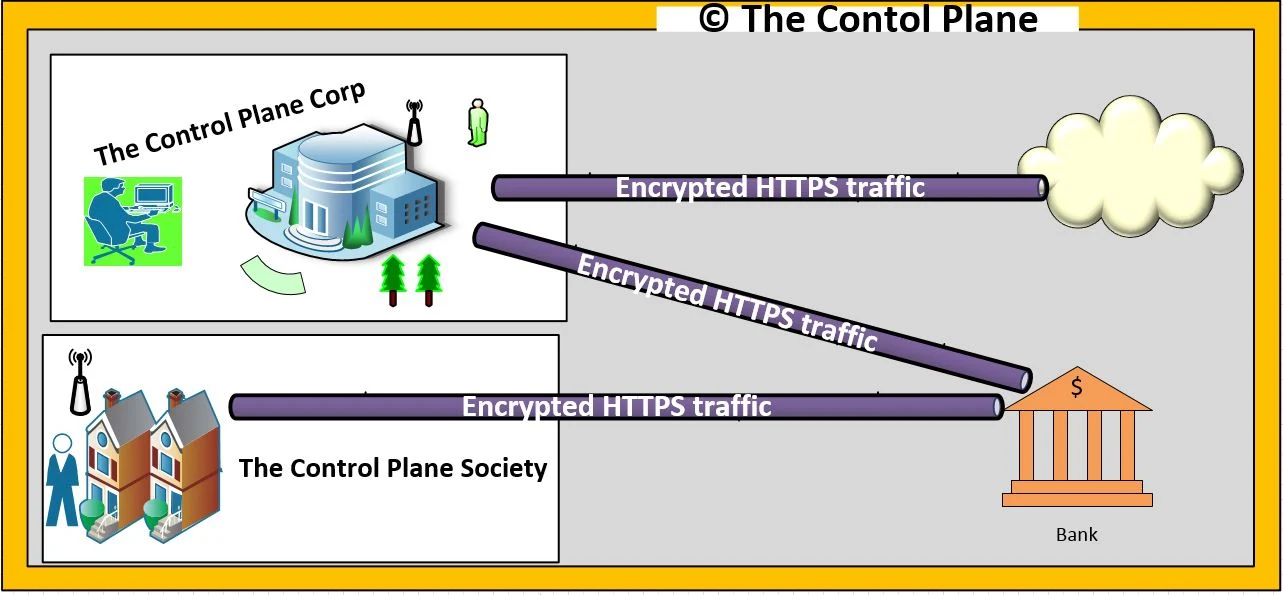
- As shown below in figure 1 the control plan corporation has user inside the office which are in traditional security designs considered as trusted user and users accessing the network from outside of office are untrusted users.
- By chance, if internal security is compromised then it could be a disaster.
- To avoid such issues Zero trust model was invented by Forrester Research Inc.Anybody on network inside or outside everybody have to follow strict security policies and check lists to access network.
- And to protect the end user security MFA multi-factor authentication came into picture.As all are using BYOD (Bring your own device) accessing internet/cloud hosted application or enterprise application from their personal mobile devices.
- In today's working environment, security is not restricted within the building,it is distributed everywhere.
Figure-1-Zero-Trust
- Let's take an example of traditional security Bob staying in the control plane society.He visit bank whenever he needs to check his balance or withdraw amount.This was because back in early 2000 there was no such strong remote security or core banking facilities exists. Banks were only secure place for transaction and security was restricted to on-premises. Bob was wasting most of the time and money going to bank.But in today's fast moving world this model is outdated and slow.Time and security means revenue.
Figure-3-Traditional-Security
- Now application are changing from desktop websites to mobile phone websites to smartphone apps.Security requirement is also changing per application based.Most of the traffic we access now a days is SSL/TLS encrypted.All the websites with https where 's' is secure are SSL/TLS encrypted websites. NSS Labs predicts that around 75 percent of total enterprise traffic will be encrypted by next year.Traditional security model always trust the SSL traffic assuming its encrypted.It means half of the traffic will pass the security uninspected which is a threat.
- Below figure shows anyone is assessing the banking or any cloud websites from office or home are https and tradition security will always send SSL traffic uninspected.
- SSL security can be used for attacks like intruders can build their own SSL website and launch attack if SSL inspection is not in place.
- Attacker can hide the malicious data the SSl enable sites any can launch attack by bypassing the security if uninspected.
Figure-2-Encrypted-Traffic
- You have got basic understanding now ,how traditional security and on prem-hardware security can not provide the complete security as per today's application and user requirement.As both are mobile not restricted to a single computer or location. SDWAN solution is application-aware and DPI (Deep packet inspection) which has list of well known ports to identify the application along with cloud SAAS application visibility as well.This features were missing in traditional WAN or security designs.
- SDWAN provides in-built security features like IPS,IDS,Firewall,Advanced Malware protection,private cloud security,public cloud security fro enterprises.
- In the diagram shown below you can see remote site is accessing public cloud.And could functionality extend till SDWA edges.Making easy choice for enterprises who are already using Multi-cloud functionality.Its make easy to connect IAAS,SAAS cloud applications.
- Let's first take an example if traditional WAN and security were in place.When remote site will access public cloud if primary link is MPLS traffic will either back hauled to data center for accessing cloud where generally cloud peering will be establish and there will be set of high end security appliances.You need set of WAN optimization devices to optimise the MPLS traffic so that like is not over utilized. Or Cloud traffic like SAAS is allowed over backup internet link where additional security is required.Last traditional scenario is using DMVPN tunnels over internet to back haul to datacenter. This will degrade the WAN performance as those tunnels will not have QoS.
- Now take SDWAN example if remote site wants to access public cloud it can use both transports.All above gaps will be overcame by SDWAN solution as both transports MPLS and internet can be used on intent basis. As now a days internet links are also improved enterprise grade. SDWAN has in-built security.For internet transport security cloud can be integrated along with baked-in SDWAN security .
- There is no requirement of WAN optimizers. As traffic will be optimised on many other factors auch as quality of link, jitter,packet loss,application criticality.And even MPLS usage will be offloaded and shared among multiple internet link transports.Making SDWAN more flexible,intelligent and secure as compare to traditional networks.
Figure-4-SDWAN-Cloud-on-Ramp
- SDWAN offers cloud exchange security as well where there is a cloud stack exchange deployed for multi-cloud security. Shown in figure 5.It is a cloud VNF which is a cloud exchange providing the security with NFV appliance which are virtual instanced hosted in cloud.
Figure-5-SDWAN-Cloud-Security-Stack
- With SDWAN solution we are getting all the required features on a single platform rather than working on single bits and pieces on multiple vendors for multiple technologies.Which will have separate management.
- VNF are virtual network functions (VNFs) that handle specific network functions like firewalls or load balancing.and Secure access service edge (SASE)services which are more focused on end.
- SDWAN SASE integration will add more value to SDWAN solutoin.SASE converges the functions of network and security point solutions into a unified, global cloud-native service.
- A SASE solution combines the capabilities of a WAN with comprehensive security functions, such as secure web gateway (SWG), cloud access security broker (CASB), firewall as a service (FWaaS), and Zero Trust network access (ZTNA) to facilitate secure network access in cloud and mobile environments.(see In picture 6).
- These all feature will be integrated in a single SDWAN solution with more insight.
Figure-6-SDWAN-SASE
- In above figure-6 you can see all the network services like SDWAN(software Defined Wide Area Network),Carrier, WAN optimization,Bandwidth aggeration,Network vendors,Network as a service , CDN ( content delivery network, or content distribution network) and security services like DNS(Domain Name System).
- SASE with SDWAN will solve all the security and network gaps in traditional networking and security model which was actually designed for on premises solutions only.









No comments:
Post a Comment
Please do not send any spam links.